You have probably seen a lot of advertisements for premium VPN services online. However, using a VPN provider to tunnel all of your internet traffic is not a smart idea, as we discussed in a previous tutorial. Contrary to what their websites claim, VPN providers typically do not give a damn about your privacy.
As these businesses manage your DNS requests and internet traffic, they have access to your whole browsing history. They may even occasionally retain records of your IP address and connection history, which might be turned over to law enforcement or stolen by cybercriminals.
Almost all websites are supplied to your browser over a safe and encrypted connection (known as HTTPS), so you usually do not need to enable a VPN connection before viewing the web. However, depending on your risk profile—also referred to as a threat model—VPNs may occasionally be helpful. Sometimes a website is restricted, making it impossible to access from a public network.
Alternatively, you might be visiting a nation where you can not access the content you are looking for, such news or services that stream music and videos. In certain situations, using a VPN is all about lowering the risk.

That’s why we are going to highlight a few different methods to set up your own encrypted VPN server at home or in a data center near you.
Use a spare home computer to run Tailscale.
Setting up a virtual network and connecting all of your devices to it is simple using Tailscale. WireGuard, a robust open source VPN protocol that functions on almost any device, is the foundation around which Tailscale is based. Tailscale has a wide range of applications. It is used by developers to gain access to distant servers.
Businesses utilize it to give their staff members access to a variety of corporate services even when they are not in the office. As an alternative to a VPN service, which encrypts and reroutes all of your internet traffic, we will use it in this instance.
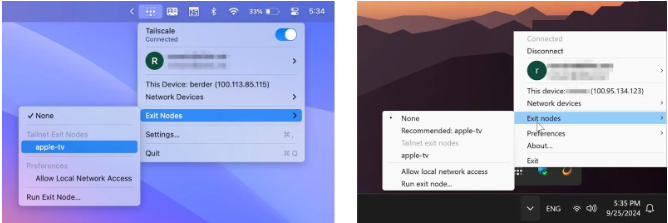
A tailnet, as used by Tailscale, is a private mesh network that enables communication between your devices. On macOS, click the Tailscale symbol in the menu bar; on Windows, click the Tailscale icon on the taskbar. After turning on Tailscale, select the “Exit nodes” menu. Select “Run exit node.”
Private keys, on the other hand, never leave your devices. No one else, not even Tailscale, can decrypt the data that passes over your VPN connection without those private keys. You may enjoy all the advantages of an encrypted VPN connection with this configuration, which eliminates the need to generate, distribute, and manage your public keys by hand. As a result, you can browse the web as if you were at home, even if you are on a very limited Wi-Fi network thousands of miles away.
“This is excellent, but I do not want to keep a computer running 24/7,” you may be thinking at this point. The good news is that you can use Tailscale to make an exit node out of an Apple TV. Your exit node will always be accessible because the Apple TV is made to run continuously so that it may be turned on and utilized whenever you choose.
You might have an Android-based set-top box or an old Android phone in a drawer if you do not use an Apple TV. You may also run an exit node on an Android device with Tailscale.
Get Tailscale installed on a Raspberry Pi.
You might wish to construct a Tailscale device yourself and connect it to your network using an Ethernet wire if your modem or router is at an odd location. Then you may purchase a Raspberry Pi, which is a small, low-cost single-board computer.
Because they include a Gigabit Ethernet port, we suggest a Raspberry Pi 4 or Pi 5. When you turn on the VPN connection, you can use that Gigabit Ethernet port to receive higher speeds if your home has a fiber connection.
With Raspberry Pi Desktop, the operating system made especially for these computers, you can flash a microSD card. To set up the Raspberry Pi, you will also need a micro-HDMI-to-HDMI connection and a USB keyboard and mouse.
The Raspberry Pi can then be turned on by connecting it to a TV or computer display. To install and operate Tailscale, you must launch the terminal and execute a few commands that are explained on Tailscale’s website.
You also need to enable IP forwarding with the following three commands on Raspberry OS:
echo 'net.ipv4.ip_forward = 1' | sudo tee -a /etc/sysctl.conf
echo 'net.ipv6.conf.all.forwarding = 1' | sudo tee -a /etc/sysctl.conf
sudo sysctl -p /etc/sysctl.confAfter the last command, run the following command:
sudo tailscale up --advertise-exit-nodeAnd this completes turning this Raspberry Pi into a Tailscale exit node.
You can now install Tailscale on your personal devices that you’re traveling with, and use the Raspberry Pi as your exit node.
You can follow the same steps with Raspberry Pi OS Lite, the operating system for the Raspberry Pi without a conventional desktop interface, if you prefer this configuration and feel at ease using the terminal.
The same steps can also be used to set up your own VPN server at a nearby data center. For about $5 a month, a number of businesses, including DigitalOcean, Vultr, Linode, Scaleway, Hetzner Cloud, and OVHcloud, provide inexpensive virtual servers.
Boot up a server and install Tailscale using their online console after setting it up with one of those cloud hosting firms. SSH, which is frequently used for remote access, may also be used to log in from your own terminal.
WireGuard on a VPS or Tailscale on Fly.io
By now, you might discover that it is not that hard to set up your own private VPN server and route all of your internet traffic over it.
Thus, you can be creative in how you set things up. For example, on Fly.io, a cloud-hosting provider that enables you to create virtual machines on the fly based on a configuration file, developer Patrick Recher has constructed a global network of Tailscale exit nodes.
With just one command line, Recher can add a server in a new region. After finishing, he shuts off and eliminates the virtual machine. Recher’s GitHub repository has additional information. Installing and configuring WireGuard directly is an option if you do not want to depend on Tailscale to manage your peer-to-peer network. You may find numerous online tutorials that will walk you through the WireGuard setup procedure. WireGuard is easy to set up, and you will pick up some tips along the road.