Over 77 cryptocurrency exchanges and banking apps in the UK, Italy, France, Spain, and Portugal are targeted by a new Android banking malware called “DroidBot.”
The new Android malware was found by Cleafy researchers, who claim that DroidBot has been in operation since June 2024 and functions as a malware-as-a-service (MaaS) platform, charging $3,000 a month for the tool. Malware builders have been used by at least 17 affiliate groups to tailor their payloads for certain targets.
Analysis of one of DroidBot’s botnets showed 776 distinct infections throughout the UK, Italy, France, Turkey, and Germany, showing a high activity despite the lack of any fresh or complex features.
Additionally, according to Cleafy, the malware seemed to be actively developing at the time and showed indications of trying to spread to other areas, such as Latin America.
DroidBot MaaS operation
The developers of DroidBot, who seem to be Turkish, give affiliates all the resources they need to launch assaults. This comprises the command and control (C2) servers, malware constructor, and a central administrative interface that allows them to give commands, retrieve stolen data, and manage their activities.
Since several affiliates share a C2 infrastructure and are given distinct identifiers, Cleafy is able to recognize 17 danger groupings.
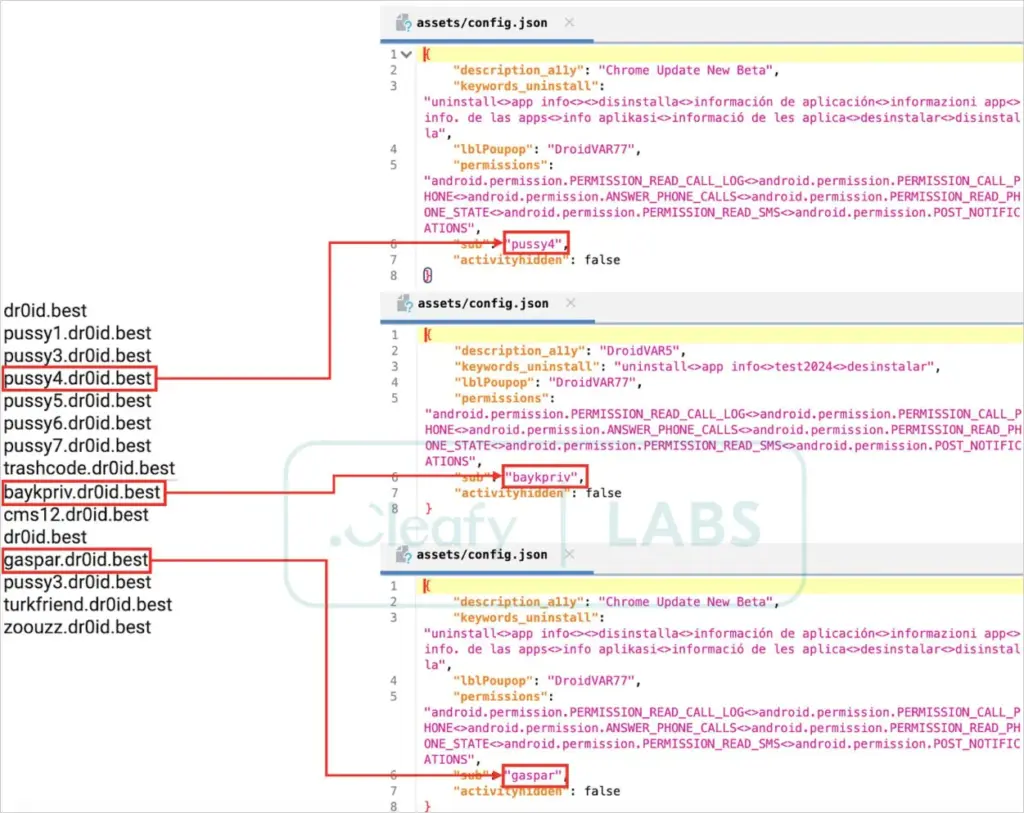
Affiliates can modify DroidBot to target particular applications, utilize multiple languages, and configure different C2 server addresses by using the payload builder.
Additionally, affiliates have access to comprehensive documentation, help from the malware’s developers, and a Telegram channel with frequent updates. All things considered, the DroidBot MaaS operation lowers the entry barrier for novice or unskilled cybercriminals.
Impersonating popular apps
DroidBot frequently poses as the Google Play Store, Google Chrome, or “Android Security” to fool users into downloading the malicious program. But in every instance, it functions as a trojan that aims to steal private data from applications.
The main features of the malware are:
- Keylogging – Capturing every keystroke entered by the victim.
- Overlaying – Displaying fake login pages over legitimate banking app interfaces.
- SMS interception – Hijacks incoming SMS messages, particularly those containing one-time passwords (OTPs) for banking sign-ins.
- Virtual Network Computing – VNC module gives affiliates the capability to remotely view and control the infected device, execute commands, and darken the screen to hide the malicious activity.
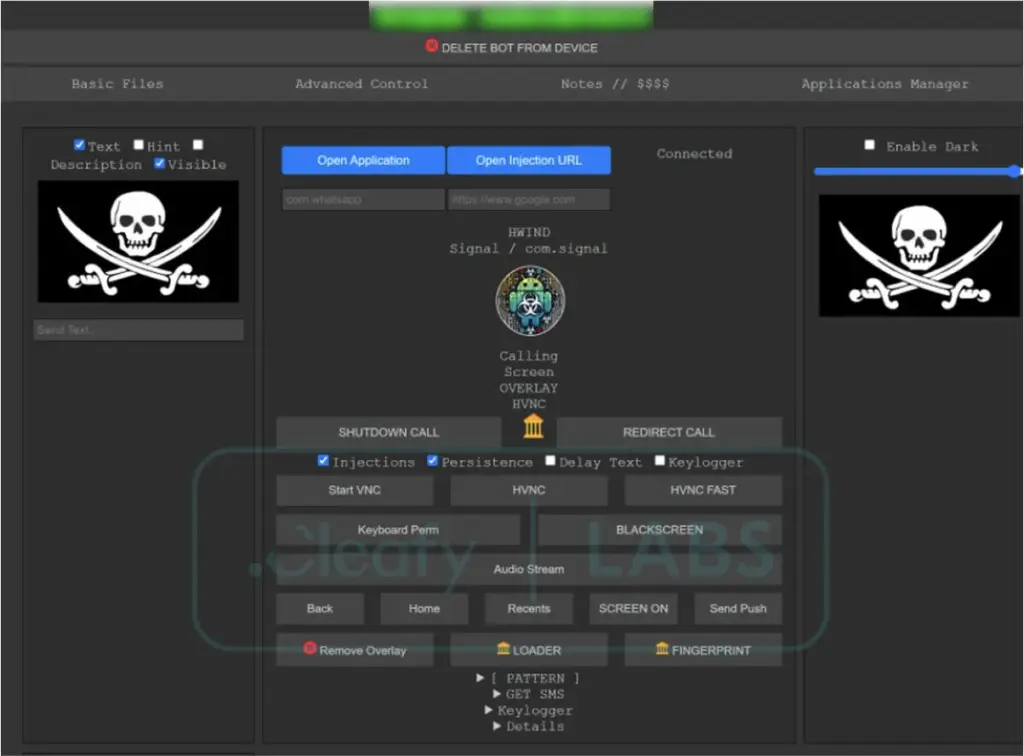
Abuse of Android’s Accessibility Services to track user activity and mimic swipes and taps on behalf of the virus is a crucial component of DroidBot’s functionality. As a result, you should be skeptical and reject an application that asks for unusual permissions, such as the Accessibility Services, as soon as you install it.
Binance, KuCoin, BBVA, Unicredit, Santander, Metamask, BNP Paribas, Credit Agricole, Kraken, and Garanti BBVA are a few of the notable apps among the 77 apps that DroidBot tries to steal credentials from.
Android users are encouraged to only download apps from Google Play, carefully review permission requests during installation, and confirm that Play Protect is turned on on their devices in order to lessen this risk.